An introduction to firewalls provides a foundational understanding of their role in network security. Firewalls act as a barrier between a trusted internal network and an untrusted external network (such as the internet). They filter incoming and outgoing network traffic based on an applied set of rules. Here are key points for an introduction to firewalls:
1. Purpose of Firewalls:
- Network Security: Firewalls are a crucial component of network security, serving as a protective barrier against unauthorized access, malicious attacks, and unwanted traffic.
- Traffic Filtering: They examine network packets and apply predetermined rules to allow or deny traffic based on specified criteria.
2. Types of Firewalls:
- Packet Filtering Firewalls: Examines packets at the network level and makes decisions based on predefined rules. It’s the most basic form of firewall.
- Stateful Firewalls: Keep track of the state of active connections and make decisions based on the context of the traffic flow.
- Application Layer Firewalls (Proxy Firewalls): Operate at the application layer of the OSI model and have the ability to inspect and filter traffic based on specific applications or services.
- Next-Generation Firewalls (NGFW): Combine traditional firewall functionality with additional features like intrusion prevention, deep packet inspection, and application awareness.
3. How Firewalls Work:
- Rule-Based Filtering: Firewalls use a set of predefined rules to determine whether to allow or block traffic based on factors like source/destination IP addresses, ports, and protocols.
- Default Deny Policy: In many cases, firewalls follow a “default deny” policy, meaning that unless a rule explicitly allows traffic, it is denied by default.
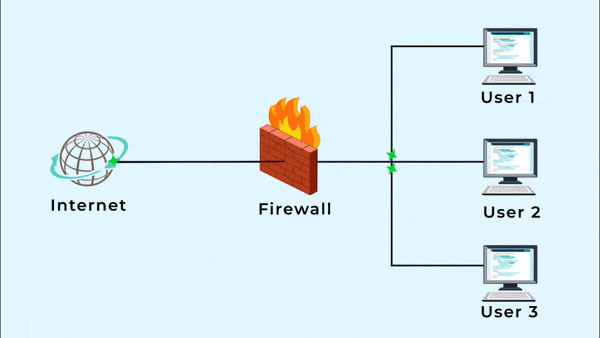
4. Placement of Firewalls:
- Network Perimeter: Placed at the boundary between an internal network and the internet. Often referred to as the first line of defense.
- Internal Firewalls: Used to segregate different parts of an internal network, providing an additional layer of protection.
- Host-Based Firewalls: Installed on individual computers or devices to control traffic at the device level.
5. Benefits of Firewalls:
- Access Control: Restricts unauthorized access to network resources.
- Traffic Monitoring: Allows for the monitoring and logging of network traffic for security analysis.
- Protection Against Malware: Can block or detect malicious traffic, helping to prevent malware infections.
6. Considerations and Best Practices:
- Regular Updates: Keep firewall rules up-to-date to address new threats and vulnerabilities.
- Testing and Validation: Thoroughly test firewall rules to ensure they function as intended without unintended consequences.
- Logging and Monitoring: Implement logging to track firewall activity for auditing and troubleshooting purposes.
- Defense in Depth: Combine firewalls with other security measures (e.g., intrusion detection systems, antivirus software) for a layered approach to security.
7. Limitations of Firewalls:
- Application-Awareness: Some advanced threats may bypass traditional firewalls, emphasizing the need for more sophisticated solutions.
- Encrypted Traffic: Firewalls may have difficulty inspecting encrypted traffic without additional decryption capabilities.
Understanding the basics of firewalls is essential for any network administrator or security professional. It forms the foundation for building a secure network infrastructure and protecting valuable data and resources from unauthorized access and cyber threats.
Found Difficult? Let’s Understand in Different Manner
Firewall: Your Digital Security Guard
Imagine a firewall as your digital security guard. It stands at the entrance of your network (like the door to your house) and decides who gets in and who doesn’t.
How Firewalls Work:
- Packet Inspection:
- Think of data packets like letters. The firewall reads the address (source and destination) on each packet to decide if it’s allowed in.
- Example: If the packet’s “address” is on the approved list, it’s allowed through. Otherwise, it’s stopped.
- Rule-Based Filtering:
- The firewall has a set of rules, like a list of who’s allowed in. If someone matches the rules, they’re let in.
- Example: You have a rule that says “Friends from the neighborhood are allowed.” If your friend comes, they’re allowed in.
Types of Firewalls:
- Packet Filtering Firewall:
- It’s like a guard checking each letter to see if it’s from a trusted sender and going to a safe destination.
- Example: If a letter comes from a known scammer, it’s blocked.
- Stateful Firewall:
- This guard not only checks letters but also remembers ongoing conversations. It knows if a response letter belongs to an earlier conversation.
- Example: If you ask a question, the response is allowed because it’s part of the ongoing conversation.
Zones and Services (For Next-Generation Firewalls):
- Zones:
- Imagine your house has different zones like the living room, kitchen, and bedroom. Each zone may have different rules.
- Example: The living room (Internet zone) may have strict rules, while the bedroom (Private zone) has more relaxed rules.
- Services:
- Think of services as activities. Some activities are allowed in certain zones, while others are not.
- Example: Web browsing (HTTP) is allowed in the living room, but cooking (FTP) is not.
Placement of Firewalls:
- Network Perimeter:
- This is like the front gate of your property. The guard here checks who’s coming in and out.
- Example: If someone has an invitation, they’re allowed in. If not, they’re turned away.
- Host-Based Firewall:
- Imagine each computer has its own mini-guard. It controls who can talk to that computer.
- Example: If a program on your computer tries to connect to the internet, the host-based firewall decides if it’s allowed.
Benefits of Firewalls:
- Access Control:
- Example: Just like you decide who comes into your room, a firewall helps decide who can access your network.
- Protection Against Malware:
- Example: If a suspicious email tries to enter your network, the firewall checks it first.
Remember, firewalls are like security guards for your digital space. They help keep your network safe and only allow trusted traffic in. Understanding how they work is essential for maintaining a secure online environment.
